Secure mobile apps is a crucial concern for app makers and users. Data breaches and security dangers are more likely to occur when mobile devices are used more often for critical transactions.
The potential for security breaches has grown with the rising use of mobile apps. Almost 3.8 billion people use smartphones globally, and Statista predicts that the figure will rise to 4.3 billion in 2023. The median price of a data breach is $3.86 million, and mobile attacks are among the most expensive, according to a survey by IBM. Given these figures, following the best mobile app security practices to safeguard user data and avoid severe financial losses is critical.
So let’s examine eight best practices for protecting mobile applications and ensure we do all possible to protect your data.
Why is Mobile App Security Important?
Secure mobile application development is essential for several reasons. The following are a few of the more significant ones:
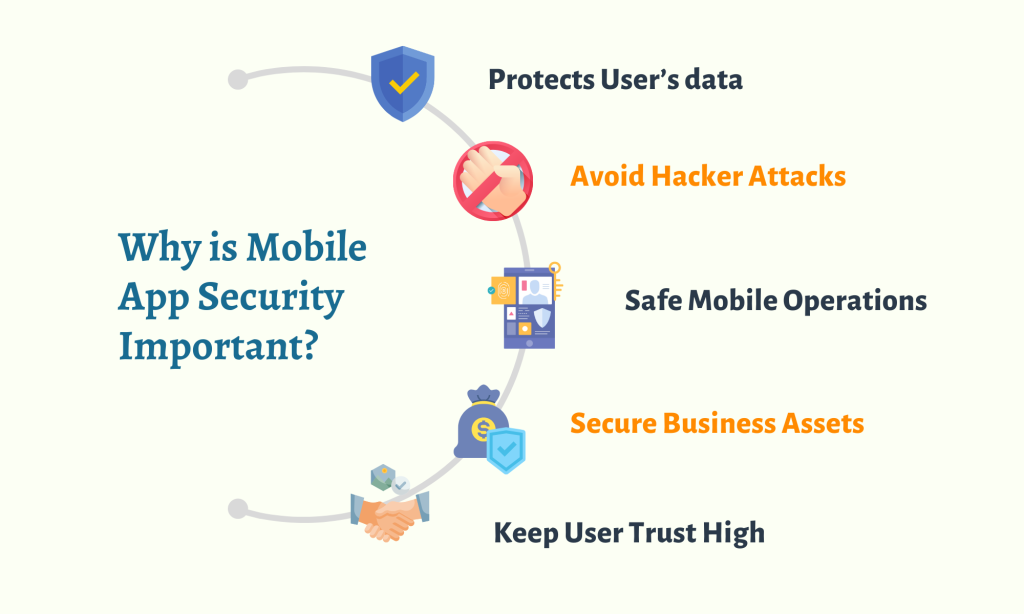
- Protects User’s data: Mobile applications gather and retain sensitive user information such as login passwords, contact details, financial information, and geolocation. Mobile app security protects this information from exploitation, theft, and unauthorized access.
- Avoid Hacker Attacks: Buffer overflow, SQL injection, and cross-site scripting are a few hacker threats against mobile apps. Hackers may use these flaws to enter the app without authorization, steal user data, insert malicious code, or trigger system failures. Developers can avoid these attacks by generating mobile app security mechanisms, including encryption, data validation, and input validation.
- Safe Mobile Operations: Money transfers, such as online shopping, mobile banking, and peer-to-peer payments, are frequently included in mobile apps. Thanks to mobile app security, these transactions are secured and guarded against fraud, phishing attempts, and other criminal behavior.
- Secure Business Assets: Companies frequently utilize mobile applications to access corporate resources, including email, client information, and other confidential material. Mobile app security ensures these resources are shielded from misuse or illegal access.
- Keep User Trust High: Mobile app security is essential to maintain users’ trust. While using mobile applications, users expect the safeguarding of their personal information. Any security flaws or data leaks can damage users’ faith in the app and the firm that created it.
8 Recommended Techniques for Secure Mobile Apps Development
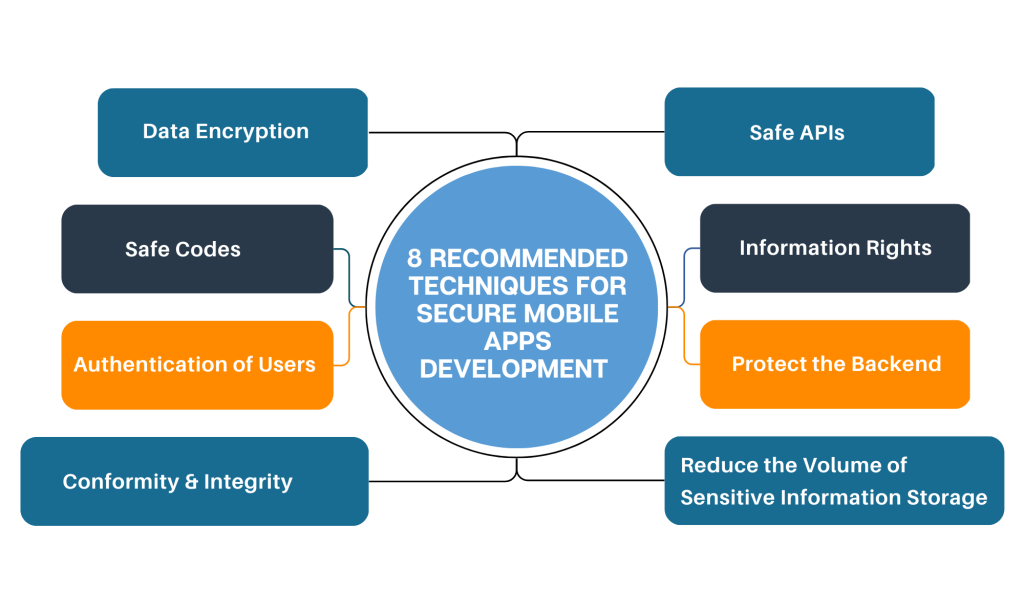
1. Data Encryption
Several consumers utilize numerous programmes across various systems and gadgets. Hence, it would help if you take precautions to guarantee that the data transferred through the programme is not made vulnerable by any system or hardware flaw.
Data encryption between apps is such an approach for accomplishing this. Data is scrambled by encryption so that attackers are unable to decipher it. The encryption is done in two ways:
Firstly, by Symmetric encryption
Secondly, by Asymmetric encryption
Secured programming is an additional recommendation for secure mobile apps. Data is encrypted and decrypted with a single key pair in symmetric encryptions. Asymmetric encryption uses separate security keys to lock and unlock simultaneously.
2. Safe Codes
Every programme has a fundamental architecture that is composed of numerous code lines. Secured codes can therefore be crucial to the safety of mobile applications.
82% of the flaws are found in the application’s source code. It implies you must ensure the raw data is clear of bugs and has no risks.
If you choose a qualified application designer, businesses can rest easy knowing that your application’s security procedures are flawless. The easiest way to verify that the script is safe and free of defects that attackers may attack is to test the mobile app development and bring in a professional.
3. Authentication of Users
The majority of UGC submissions come from mobile applications (user-generated content). Without a reliable solution for user identification, UGC may be at risk of cyberattacks. Through methods such as social engineering, fraudsters may acquire individuals’ sensitive data.
Via UGC, they may easily insert harmful code after gaining entry to user accounts. In contrast to the conventional authentication procedure, a further layer of protection is added via OTP, tokens, encryption keys, or other methods. You might use multiple-factor verification or another user authentication method here.
As an illustration, multi-factor authentication helps individuals to confirm their identity using the OTP they get on their smartphone. Conformity is a crucial component of mobile application protection.
4. Conformity & Integrity
Each mobile app must meet standards and undergo security screening before deployment. Under the guidance of the application store, there can be certain safety precautions that developers must adhere to. These controls may be for an app’s installation or downloading procedure.
Modern smartphones use app stores to make code-signed programmes and other software available to consumers. This procedure ensures that a system only delivers apps that are tested thoroughly.
Developers may upload their programmes to the app store, where their identity and the safety needs of the applications are verified. If everything complies with the criteria of the operating system, the software becomes available for download.
Although this sounds difficult, multiple code sign solutions simplify it. Considering your application’s safety and reliability, you may also quickly obtain a cost-effective, low-cost code signing certification. It proves that the code is from scratch and that the publishing is valid.
This certification assists programmers in encrypting identity-related data, which afterwards decodes using a public key made available to consumers. You must also know the application programming interfaces (APIs) regarding app safety.
5. Safe APIs
APIs are necessary for third-party integrated services and capability enhancement. It makes it possible for disparate systems to communicate with one another and share data. Yet, you require safe APIs and shouldn’t disclose the data transferred for more excellent app safety. Using permissions for data accessibility is the greatest technique to guarantee API security.
6. Information Rights
Finding data privileges is another way to guarantee that your application is not vulnerable to harmful cyberattacks. It will prevent someone with bad intentions who lacks data access from gaining unauthorized access to private information. When giving restricted users entry to confidential information, use the rule of least privilege.
7. Protect the Backend
Most mobile apps utilize a client-server architecture. Most developers believe an API can be accessed by an application specifically designed to do so. Nevertheless, since API authentication and transport protocols might vary from one system to another, you must test all your APIs in line with the mobile system you intend to build for. Security procedures must be in place to protect from malware activity on backend systems.
8. Reduce the Volume of Sensitive Information Storage
Developers favor storing sensitive information in the phone’s local storage to keep consumers from seeing it. Yet, it’s an excellent method to avoid keeping sensitive information because doing so might raise the potential threat. Employ an encrypted data container or a key chain when you’ve got no choice but to keep the information. The auto-delete option, which instantly removes information after a set time, should also be added to decrease the record.
Conclusion
Building secure mobile apps is essential for several reasons. By giving security a first priority when creating mobile apps, developers can make sure that consumers can use their apps with trust and confidence, knowing that their data is protected.
At HR Tech LLC, we recognise the need to create the greatest mobile applications while simultaneously placing a high priority on security. In order to make sure that the mobile apps for our clients are safe, dependable, and easy to use, our team of skilled developers is dedicated to putting the most recent security best practices into effect. To find out more about our secure mobile apps development services, get in touch with us right away.